Administrator
Handbook |
TOC |
Trap and Event filter creation
All filters are defined in the trapfilter.txt file located in the /bin directory of the LoriotPpro software. This file is a standard text file that you could edit with the Notepad program of Windows. The file creation could be made manually or extract from the documentation or by using the included tools.
The file is structured in two parts.
1. The first one defines the Trap filters
and their associated actions
2. The second one defines the local or remote event
filters, respecting the LoriotPro format, and their associated actions.
LoriotPro includes a ‘Trap managers’ listening on UDP port 162. The software decodes different version of SNMP trap but the filter syntax remains the same for all of these versions.
To filter a trap you should know its name, the software will use the SNMP ObjectID received in the Trap to match the correct filter. If you want to filter a received Trap you could use the « Trap filter Wizard » of the trap window contextual menu.
Traps are initially defined in MIB files. If MIB files are compiled (added to LoriotPro) the exact name of the Trap will be recognized and you’ll have to use it in the filter. Otherwise, the name will be under its OID format and you will have to use it in the filter
![]() Warning: If you compile MIB files with the trap definitions of already declared
filters using the OID format you’ll have to modify it with their real name to
get them work.
Warning: If you compile MIB files with the trap definitions of already declared
filters using the OID format you’ll have to modify it with their real name to
get them work.
A simple way of finding a Trap name that you want to filter is to look at the ObjID column in the Trap window and to use the exact displayed name in the filter.
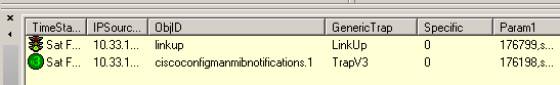
ObjID column in the Trap window
In the example above, two traps have been received, if you want to filter the SNMP V3 notification, use the name ciscoconfigmanmibnotifications.1.
The same Trap in SNMP v1 has another name.
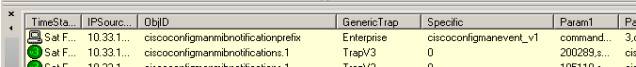
In this example the SNMP v1 Trap has the name :
ciscoconfigmanmibnotificationprefix .
This Trap is defined in the Cisco MIB :
Fichier : CISCO-CONFIG-MAN-MIB.my (extract)
ciscoConfigManEvent TRAP-TYPE
-- Reverse mappable trap
ENTERPRISE ciscoConfigManMIBNotificationPrefix
VARIABLES {
ccmHistoryEventCommandSource, ccmHistoryEventConfigSource,
ccmHistoryEventConfigDestination }
-- Status
-- mandatory
DESCRIPTION
"Notification of a configuration management event as
recorded in ccmHistoryEventTable."
::= 1
To create filters, you could modify the file trapfilter.txt with a text editor or use the « Trap Filter Wizard ». You should call it from the contextual menu after having selected the Trap type to filter in the Trap window.
Traps Filter wizard option in the Trap contextual menu
This option leads to the trap filter creation window.
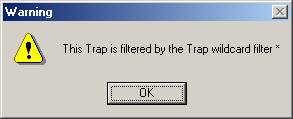
If a Trap filter already exists, the program offers you to add an action to this Trap.
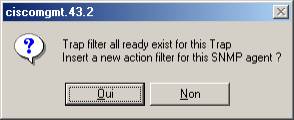
The Trap action creation window appears with the known parameter of the agent. Select the actions that you want to realize on the next incoming trap of this type and coming from this agent.
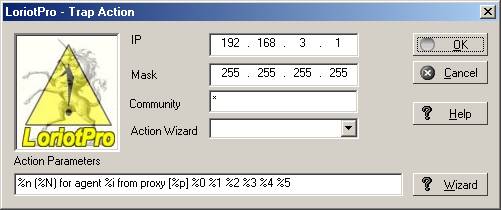
Trap action Wizard window
If the Trap is not yet defined in the filter tree, the Wizard offers you to create a new entry.
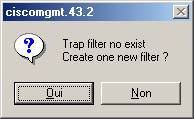
The Wizard opens a Trap creation window with the selected Trap parameters.
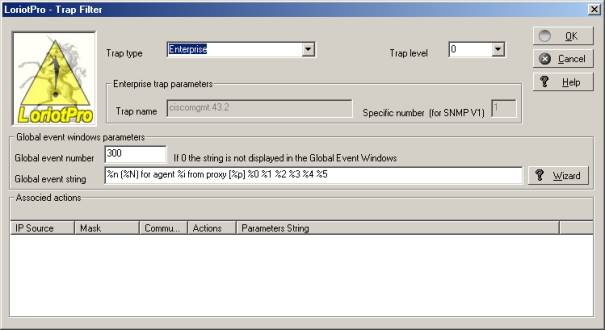
Trap Filter creation Wizard window
If you refuse the automatic creation, at least you can use the proposed syntax to put in the trapfilter.txt file.
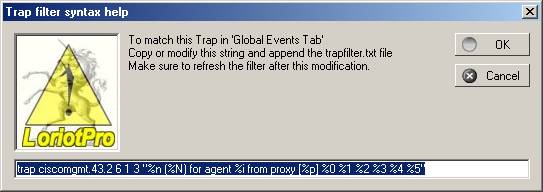
Trap filter syntax
Trap filter creation in the Filter window
A new Trap could be directly created from the Trap window.
Select the Traps Filters node object in the tree and call the contextual menu « New Trap Filter/Action ».
The Trap filter creation window is displayed.
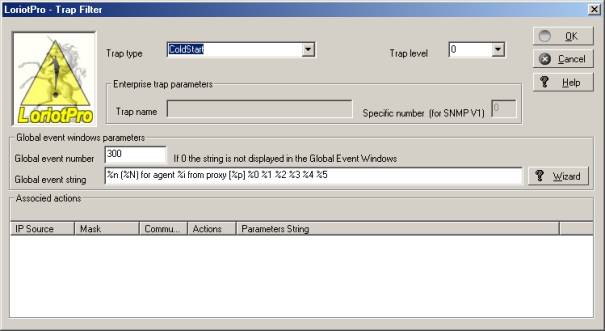
The first task consists of defining a name for the Trap filter. If the Trap is a standard Trap, select it from the combo box. If the Trap is of ‘Enterprise type select it from the Enterprise type combo box, this will unlock the « Trap name » filed.
Use all received information in the Trap window and the documentation syntax table to complete the fields. The Wizard button calls the help window that guides you for creating the character string including the variables.
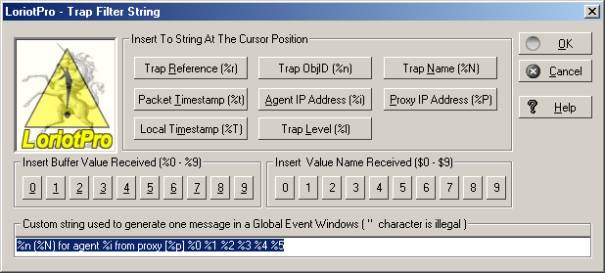
Trap filter string (Wizard)
Once the Trap filter name known, you should define all associated parameters. A filter is defined by only one line without carriage return. A filter contains 6 to 7 parameter in a specific order.
Example
trap ciscoConfigManMIBNotificationPrefix 6 1 3 "%n (%N) for agent %i from
proxy [%p] %0 %1 %2 %3 %4 %5"
Table of Trap filter syntax
| Options |
Examples |
Definitions |
||||||||||||||||||||||
| Trap |
trap |
This keyword informs the compiler that it is a Trap filter. |
||||||||||||||||||||||
| name |
ciscoConfigManMIBNotificationPrefix |
The Trap name. Remark If you use the name * then all received Trap no yet filtered will be filtered by this line. When using the Wizard, a message inform you that your filter line will be placed after such line with an *. |
||||||||||||||||||||||
| The generic Trap type |
6 |
This parameter is used by Trap SNMP v1 and define Standard Traps In SNMP v1, six generic Traps are defined, one complementary is called “specific”
|
||||||||||||||||||||||
| The specific trap type |
1 |
Use in SNMP v1 when the generic type of the Trap is 6 (previous parameter) else this value is 0. |
||||||||||||||||||||||
| The severity level |
3 |
Value from 0 to 10 are use to assign a level of severity to the Trap. The level allows a display of Trap in different colors in the Global Event window. |
||||||||||||||||||||||
| The message to display in the Global Events window |
"%n (%N) for agent %i from proxy [%p] %0 %1 %2 %3 %4 %5" |
This parameter is a character string delimited by quotations. The message body that should be display in the Global Events window. Variable start by the % or $ character followed by a reference letter use by the compiler to replace them by their value. Customized variables could be used in the string.
|
||||||||||||||||||||||
| Event number assigned (optionnal) Higher than 10000. |
10002 |
By default, Trap forwarded to the Global Event window us the number 300. You could customize your by selecting another number higher than 10000. That allows you to create dedicated Event filters. . |
Examples
trap ciscoMgmt.41.2 6 1 1 "%n for Agent %i proxy [%p] $0->%0
$1->%1 $2->%2 $3->%3"
trap ciscoMgmt.43.2 6 1 1 "%n for Agent %i proxy [%p] $0->%0 $1->%1
$2->%2 $3->%3"
trap cisco 6 1 3 "%n (%N) for agent %i from proxy [%p] : %0 %1 $2/%2
ByteIn/%3 ByteOut/%4 $5/%5"
trap loriotidsprobe 6 1 3 "%n (%N) for agent %i from proxy [%p] : %0
%1 $2/%2 ByteIn/%3 ByteOut/%4 $5/%5"
trap ciscoSyslogMIBNotificationPrefix 6 1 3 "%n (%N) for agent %i from
proxy [%p] %0 %1 %2 %3 %4 %5"
trap ciscoConfigManMIBNotificationPrefix 6 1 3 "%n (%N) for agent %i from
proxy [%p] %0 %1 %2 %3 %4 %5"
trap LinkDown 2 0 6 "%r for %n from %i Interface %1 at %t Description
%1 Type %2 Status %3" 10002
The reception of a Trap could trigger an action. You could trigger action on filter conditions based on the packet source address or the SNMP community. Actions are located in the filter file after the Trap definition. The key work “action” followed by five parameters should be used on each line defining a new action.
Example
action 0.0.0.0 0.0.0.0 * wave "wave/linedown.wav"
Table of syntaxes of Trap associated actions
| Parameters |
Examples |
Definitions |
| action |
action |
This keyword defines the beginning of an action line use by the compiler |
| IP |
0.0.0.0 |
The two following parameters are used to trigger an action if the source address of the packet match the filter. The rule below is applied : IF IP_SOURCE_RECEIVED AND IP_MASK = IP THEN action Example : With IP received = 10.33.10.121 If rule with IP = 0.0.0.0 IP_MASK =0.0.0.0 then all IP addresses trigger the action) If rule with IP=10.33.0.0 IP_MASK=255.255.0.0 then the action is triggered because 10.33.10.121 pertains to network 10.33.0.0 If rule with IP=20.0.0.0 IP_MASK=255.0.0.0 then no action is triggered because 10.33.10.121 does not pertain to network 20.0.0.0) To select a unique address example : 192.168.10.1 code the action below Action 192.168.10.1 255.255.255.255 |
| IP Mask |
0.0.0.0 |
Define above. |
| Community |
* |
The SNMP community that should be receive to trigger the action (Only in SNMP V1 et V2c). The * sign works has wildcard. Warning: If you use SNMP v3, use the * and the advanced parameter of the host that should be defined for this object. |
| Action types |
Wave |
The type of action to trigger if all the 3 previous conditions are satisfied. See next table for action types |
| command |
"wave/linedown.wav" |
A character string that is used as line parameter by the excutable program See next table for action types |
Tableau des actions associées aux Traps
| Actions |
Command |
| wave |
Play a wave file : The string of command line parameters should contain the full path to a wave file. The string could contain variables. Example: |
| trap |
Forward the v1 or v2c Traps to another server. Example: |
| winrun |
Start a Windows type program : The string of command line parameters should contain the full path to an Window executable file. The string could contain variables Example: |
| dosrun |
Start a DOS type program : The string of command line parameters should contain the full path to an Window executable file. The string could contain variables identical to the Trap filter string Example: |
| syslog |
Send a Syslog message : The string of command line parameters contains the IP address of the Syslog server and others variables. Example: |
| smtp |
Create a Mail message in the Mail spooler The string of command line parameters should contain The E-mail address and other variables. Example smtp "unknow@domain.com Authentication fail %i %m " |
| custom |
Display the Trap in the custom window 1 to 3 and their variables. Example: |
| nul |
Do nothing |
Table of variables
| Variables | Meaning |
| %r |
Reference |
| %i |
IP address of the SNMP agent |
| %p |
Source IP address of the Trap packet |
| %t |
Timestamp contain in the Trap, %t display the Timestamp. |
| %T |
Display the local Timestamp. |
| %0 à %9 |
Trap specific parameters values if they exist |
| $0 à $9 |
The SNMP name of the previous parameters |
| %n |
The Trap SNMP ObjID. |
| %l |
The severity level |
| %N |
The Trap name if it exists |
Examples
trap Authentication 4 0 3 "%n (%N) for agent %i from proxy
[%p] %0 %1 %2 %3 %4 %5"
action 10.33.10.121 255.255.255.255 public trap "10.33.10.129"
action 10.33.10.121 255.255.255.255 public wave "wave/ding.wav"
action 0.0.0.0 0.0.0.0 * syslog "10.33.10.126 %r for %n from %i from
proxy [%p] Request from station [%0]"
trap LinkUp 3 0 4 "%r for %n from %i Interface %1 at %t Description %1
Type %2 Status %3" 10001
action 0.0.0.0 0.0.0.0 * wave "wave/lineup.wav"
The reception the ‘Authentication’ standard Trap will generate a message in the Global event window
If the source address of the sending agent satisfy the condition actions will be realized. If this address is 10.33.10.121, three actions will be realized.
1. A Trap will be forwarded to server
10.33.10.129
2. The ding.wav sound will be played.
3. A Syslog message will be sent to the server 10.33.10.126.
Remark: The variable used in the string are the same as those used in the Trap filter.
![]() Warning: It could no be several filter for the same Trap but a Trap could trigger
several actions.
Warning: It could no be several filter for the same Trap but a Trap could trigger
several actions.
It is possible to insert an action from the Contextual Trap window menu with the « Trap Filter Wizard » option.
In the Trap filter tree, select the Trap to which you want to add an action.
New Trap Filter/Action…

A new Window is displayed.
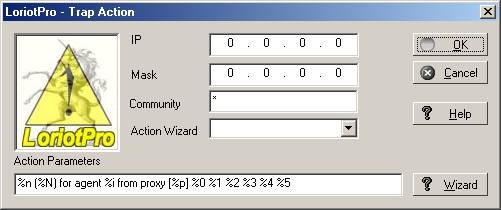
This window uses the parameters previously.defined Each action offers you an customized window.
Wave action :
Select a wave file. You should have a wav file player installed.
WinRun and DosRun Action:
Select a program.
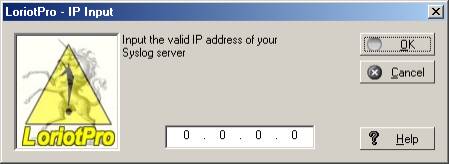
Syslog action :
Enter the IP address of the Syslog server.
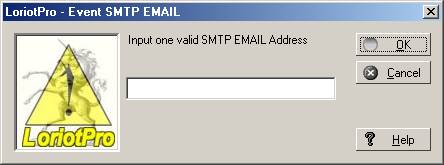
SMTP action :
Enter the Email address of the receiver.
![]() Warning: The SMTP service should be installed for this option to work.
Warning: The SMTP service should be installed for this option to work.
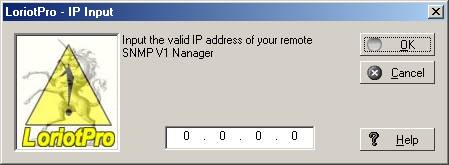
Trap action :
Enter IP address of the management server.
A filter for an Event is define by a line in the trapfilter.txt without Crand starting with the keyword event. An Event filter could contain six to seven parameters.
Example
event 210 0.0.0.0 0.0.0.0 4 wave "wave/loriotgoup.wav"
Event filters syntaxThe following table displays the syntax to use in Event filter.
Table of Event filters syntax
| Parameters |
Examples |
Definitions |
|
| event |
Event |
The keyword event starts each new line defining a filter and is uses by the compiler. |
|
| number |
210 |
The reference number of the event The list is defined in the events.txt file. |
|
| IP |
0.0.0.0 |
The two following parameters are used to trigger an action if the source address of the packet match the filter. The rule below is applied : IF IP_SOURCE_RECEIVED AND IP_MASK = IP THEN action Example : With IP received = 10.33.10.121 If rule with IP = 0.0.0.0 IP_MASK =0.0.0.0 then all IP addresses trigger the action) If rule with IP=10.33.0.0 IP_MASK=255.255.0.0 then the action is triggered because 10.33.10.121 pertains to network 10.33.0.0 If rule with IP=20.0.0.0 IP_MASK=255.0.0.0 then no action is triggered because 10.33.10.121 does not pertain to network 20.0.0.0) To select a unique address example : 192.168.10.1 code the action below Action 192.168.10.1 255.255.255.255 |
|
| The level of severity assign to this event |
4 |
Value from 0 to 10 are use to assign a level of severity to the Trap. The level allow a display of Trap in different colors in the Global Event window. |
|
| Action type |
Wave |
The type of action to trigger if all the IP address condition is satisfied. See next table. |
|
| command |
"wave/linedown.wav" |
A character string, quote delimited, containing the parameter use in the command line. See next table. |
|
Tableau des variables utilisées avec les filtres d’événements
| Variables |
Value assigned |
| %r %R |
Event number |
| %i %I |
IP address of the sending agent |
| %T |
Local Time stamp |
| %l |
Severity level |
| %m |
The message generated by the Event |
Tableau des actions associées aux événements
| Actions |
Commande |
| wave |
Play a wave file : The string of command line parameters should contain the full path to a wave file. The string could contain variables. Example: |
| winrun |
Start a Windows type program : The string of command line parameters should contain the full path to an Window executable file. The string could contain variables Example: |
| dosrun |
Start a DOS type program : The string of command line parameters should contain the full path to an Window executable file. The string could contain variables identical to the Trap filter string Example: |
| syslog |
Send a Syslog message : The string of command line parameters contains the IP address of the Syslog server and others variables. Example: |
| smtp |
Create a Mail message in the Mail spooler The string of command line parameters should contain The E-mail address and other variables. Example : |
| custom |
Display the Trap in the custom window 1 to 3 and their varaibles. Example: |
| route |
Route the event to another LoriotPro server. The command line contain the IP address destination and the UDP port use on the remote LoriotPro for Event receiving. Example: |
| Nul |
Do nothing |
Remark: You could define several filters for the same Event type with different associated actions and different address filters.
Example
event 101 0.0.0.0 0.0.0.0 1 wave "wave/%igodown.wav"
event 101 10.33.10.121 255.255.255.255 4 custom 1
event 101 0.0.0.0 0.0.0.0 2 custom 2
event 10002 0.0.0.0 0.0.0.0 4 custom 2
event 101 10.0.0.0 255.0.0.0 1 wave "wave/hostgodown.wav"
event 101 0.0.0.0 0.0.0.0 1 smtp "ludo4@test.com %i form %I host go down"
event 100 0.0.0.0 0.0.0.0 1 wave "wave/%igoup.wav"
event 100 0.0.0.0 0.0.0.0 1 winrun "telnet %i"
event 100 20.0.0.0 0.0.0.0 1 wave "wave/chord.wav"
event 100 30.0.0.0 0.0.0.0 1 wave "wave/chord.wav"
event 101 00.0.0.0 0.0.0.0 1 route "10.33.10.122 5001"
event 210 0.0.0.0 0.0.0.0 4 wave "wave/loriotgoup.wav"
event 211 0.0.0.0 0.0.0.0 4 wave "wave/loriotgodown.wav"
event 214 10.33.10.121 255.255.255.255 1 wave "ding.wav"
event 214 0.0.0.0 0.0.0.0 1 null "empty"
event 1 10.33.10.121 255.255.255.255 1 wave "wave/ding.wav"
event 100005 0.0.0.0 0.0.0.0 4 dosrun "toto.bat '%m'"
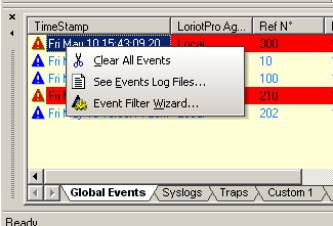
Like in the Trap window, the Global Event window has a contextual menu with the option Event Filter Wizard.
Select an Event from the Global Event Window and right click to call the contextual menu.
>Event Filter Wizard…
The creation of a new action for this Event is proposed. The current event parameter will be used to define the action.
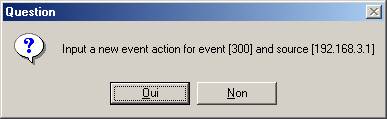
The filter creation window is displayed with the current action parameters.
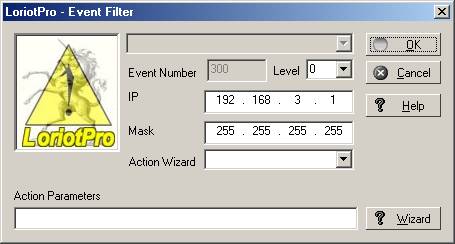
Event filter window(Wizard)
The List box Action Wizard allows you to select an action type among the list. The Action parameter allows you to define the additional parameters that will be used by the program.
Wave action :
Select a wave file. You should have a wav file player installed.
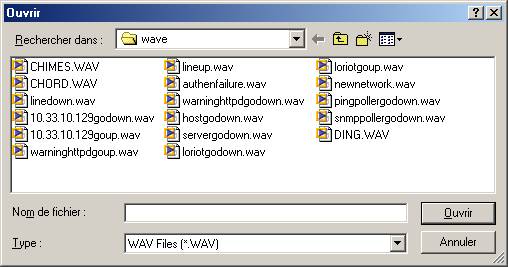
WinRun and DosRun Action:
Select a program.
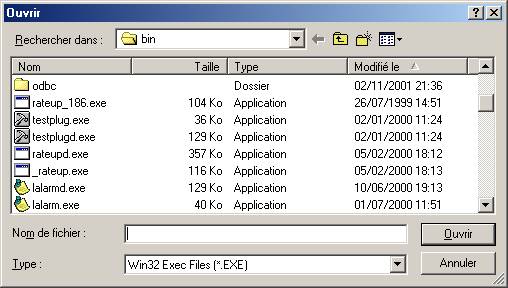
Syslog action :
Enter the IP address of the Syslog server.
Custom action :
A window is displayed asking you to select in which Custom window you want to display the action.
Event Custom Selection (Wizard)
Route action :
Enter the address of the LoriotPro server to which you want to forward the event.
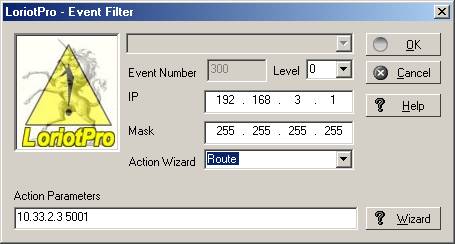
![]() Warning: The software uses by default the destination port 5001 when forwarding
Events. If you want to specify another port number modify the line parameter
like in the example below
Warning: The software uses by default the destination port 5001 when forwarding
Events. If you want to specify another port number modify the line parameter
like in the example below
SMTP action :
Enter the Email address of the receiver.
![]() Warning: The SMTP service should be installed for this option to work.
Warning: The SMTP service should be installed for this option to work.
We have seen that the Event Filter Wizard allows you to create filters in a simple way. The Wizard could also be called directly from the Filter tree by selecting an Event in the tree and right clicking.
>New Event Filter…

This time, an empty creation window is displayed.
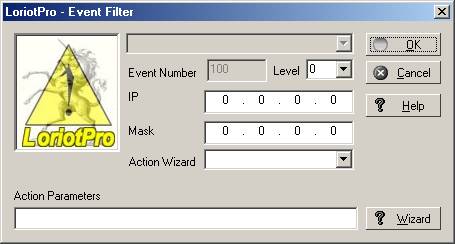
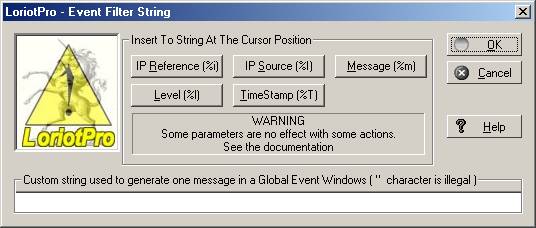
The Wizard button calls the advanced window that help you to create the character string that will be used in the command line.
![]() Warning: The creation window adds the new created filter at the end of the bottom
of the tree and the trapfilter.txt is automatically saved when you leave it.
If you want to re-order the filter you should manually edit the trapfilter.txt
file, save it after modification and do a refresh of the window from the menu
« Configure>Traps/Events Filter ».
Warning: The creation window adds the new created filter at the end of the bottom
of the tree and the trapfilter.txt is automatically saved when you leave it.
If you want to re-order the filter you should manually edit the trapfilter.txt
file, save it after modification and do a refresh of the window from the menu
« Configure>Traps/Events Filter ».
Refresh Traps Filters Menu
The default trapfilter.txt file
The trapfilter.txt is located in the /bin directory. It contains few trap and event filters that could help you as examples to create and customize you management server.
Trapfilter.txt file
# trapfilter.txt file used by LoriotPro (c) 1999-2002, all rights
Reserved Ludovic Lecointe
#
# This file was loaded at the start of LoriotPro
# It is possible to refresh the trap filter in the event docking window with
the context menu
# or when you go to the mib compiler module
#
# For the smtp action install and configure the SmtpEventScheduler.sp service
plugin
#####################################################################################
#
# Available parameters and syntax for trap string
#------------------------------------------------
#
# %r reference
# %i agent ip address
# %p proxy ip address
# %t timestamp gived by agent in trap packet
# %T timestamp local
# %0 to %9 buffer parameters of the trap if exist
# $0 to $9 name parameters of the trap if exist
# %n ObjId of the trap
# %N name of the trap if exist
# %l level of the trap
#
# 7 colonnes define the trap
#
# 1 trap
# 2 ObjID for trap generic 6
# 3 trap generic number 1 a 6 (1-5) reserved 6 interprise: put 6 for notification
V2c or V3
# 4 trap specific number x for interprise trap: put 0 for notification V2c or
V3
# 5 trap level for syslog or action in event manager
# 6 "string with variables"
# 7 event level (300 by default or sup to 10000 for custom.
# if 0 the event was not generated but the only the
actions
#
# Available parameters and syntax for action string (a same then for trap)
#------------------------------------------------
#
# 6 colonnes define trap action
#
# 1 action keyword
# 2 ip add
# 3 ip mask
# 4 community (* = any)
# 5 action (wave winrun dosrun syslog)
# wave "wave/linedown.wav"
# winrun "telnet %i"
# dosrun "dir *.*"
# syslog "10.33.10.126 string
with variable"
# trap "10.33.10.129" (reroute the trap to
10.33.10.129)
# smtp "name@domain.com string with variable"
# 6 "string with variable running"
#
#
#
# Available parameters and syntax for event string
#------------------------------------------------
#
# %i %I agent ip address
# %m message of the event (the '<x>' information at the start of the message
is replaced
# by ' x ' if you use the dosrun or winrun action.
# %r %R ref of the event (number)
# %T timestamp local
# %l level for this action
#
# 7 colonnes define event action
#
# 1 event keyword
# 2 number (reference of the event see events.txt file)
# 3 ip add
# 4 ip mask
# 5 level (number) assign one level for this event and this ip/mask selection
# 6 action (wave winrun dosrun syslog custom null)
# wave "soubd/ding.wav"
# winrun "telnet %i"
# dosrun "dir *.*"
# syslog "10.33.10.126 string
with variable"
# smtp "name@domain.com string with variable)
# custom 1 (1 2 or 3 to display the alert in custom alert
list box)
# null null
# 7 "string with variable running"
################################################################################
#########################################################################
#trap /action configuration
#########################################################################
#V2c or V3 notification sample
trap enterprises.9.9.43.2.0.1 6 0 1 "%n for Agent %i proxy [%p] $0->%0
$1->%1 $2->%2 $3->%3"
action 10.33.10.121 255.255.255.255 * wave "wave/chord.wav"
trap ciscoMgmt.41.2 6 1 1 "%n for Agent %i proxy [%p] $0->%0 $1->%1
$2->%2 $3->%3"
trap ciscoMgmt.43.2 6 1 1 "%n for Agent %i proxy [%p] $0->%0 $1->%1
$2->%2 $3->%3"
trap cisco 6 1 3 "%n (%N) for agent %i from proxy [%p] : %0 %1 $2/%2
ByteIn/%3 ByteOut/%4 $5/%5"
trap loriotidsprobe 6 1 3 "%n (%N) for agent %i from proxy [%p] : %0
%1 $2/%2 ByteIn/%3 ByteOut/%4 $5/%5"
trap ciscoSyslogMIBNotificationPrefix 6 1 3 "%n (%N) for agent %i from
proxy [%p] %0 %1 %2 %3 %4 %5"
trap ciscoConfigManMIBNotificationPrefix 6 1 3 "%n (%N) for agent %i from
proxy [%p] %0 %1 %2 %3 %4 %5"
trap LinkDown 2 0 6 "%r for %n from %i Interface %1 at %t Description
%1 Type %2 Status %3" 10002
#action 10.33.10.121 255.255.255.255 public wave "wave/ding.wav"
#action 10.33.10.121 255.255.255.255 * winrun "telnet %i"
action 0.0.0.0 0.0.0.0 * wave "wave/linedown.wav"
trap LinkUp 3 0 4 "%r for %n from %i Interface %1 at %t Description %1
Type %2 Status %3" 10001
action 0.0.0.0 0.0.0.0 * wave "wave/lineup.wav"
trap Authentication 4 0 3 "%r for %n from %i from proxy [%p] Request from
station [%0]" 10005
#action 10.33.10.121 255.255.255.255 public trap "10.33.10.129"
#action 10.33.10.121 255.255.255.255 public wave "wave/ding.wav"
#action 0.0.0.0 0.0.0.0 * syslog "10.33.10.126 %r for %n from %i from
proxy [%p] Request from station [%0]"
#########################################################################
#event configuration see events.h and events.txt file
#########################################################################
#define EVENT_NEWHOST 1
#define EVENT_NEWNETWORK 2
#define EVENT_HOSTGOUP 100
#define EVENT_HOSTGODOWN 101
#define EVENT_HOSTGOPOLLED 102
#define EVENT_HOSTGONOPOLLED 103
#define EVENT_HTTPDGOUP 200
#define EVENT_HTTPDGODOWN 201
#define EVENT_POLLINGGOUP 202
#define EVENT_POLLINGGODOWN 203
#define EVENT_POLLINGPINGGOUP 204
#define EVENT_POLLINGPINGGODOWN 205
#define EVENT_POLLINGSNMPGOUP 206
#define EVENT_POLLINGSNMPGODOWN 207
#define EVENT_PLUGINLOADERROR 208
#define EVENT_LORIOTGOUP 210
#define EVENT_LORIOTGODOWN 211
#define EVENT_V3AUTHERROR 212
#define EVENT_V3REPLAY 213
#define EVENT_V3ERROR 214
#define EVENT_TRAP 300
#########################################################################
event 200 0.0.0.0 0.0.0.0 2 wave "wave/warninghttpdgoup.wav"
event 201 0.0.0.0 0.0.0.0 2 wave "wave/warninghttpdgodown.wav"
#event 101 0.0.0.0 0.0.0.0 1 wave "wave/hostgodown.wav"
#event 101 10.0.0.0 255.0.0.0 1 wave "wave/hostgodown.wav"
#event 101 10.33.10.121 255.255.255.255 4 custom 1
#event 100 0.0.0.0 0.0.0.0 1 wave "wave/%igoup.wav"
#event 100 20.0.0.0 255.0.0.0 1 wave "wave/ding.wav"
#event 100 30.0.0.0 255.0.0.0 1 wave "wave/ding.wav"
event 210 0.0.0.0 0.0.0.0 4 wave "wave/loriotgoup.wav"
event 211 0.0.0.0 0.0.0.0 4 wave "wave/loriotgodown.wav"
#event 2 0.0.0.0 0.0.0.0 2 wave "wave/newnetwork.wav"
#event 1 10.33.10.121 255.255.255.255 1 wave "wave/ding.wav"
#event 214 10.33.10.121 255.255.255.255 1 wave "ding.wav"
#event 214 0.0.0.0 0.0.0.0 1 null "empty"
#event 300 0.0.0.0 0.0.0.0 1 syslog "10.33.10.129 %m"
#event 300 0.0.0.0 0.0.0.0 1 smtp "unknow@domain.com %m"
#event 10005 0.0.0.0 0.0.0.0 1 smtp "unknow@domain.com Authentication
fail %i %r %R %m"
 www.loriotpro.com
www.loriotpro.com |
|